Shift
Video Demonstration
Shift is Caido's official AI/LLM plugin that can be instructed to automate tasks in your security assessments.
In this tutorial, you will learn how to use the plugin's two main components: Shift Core and Shift Agents.
INFO
Shift is available for installation in the Official tab of the Plugin interface.
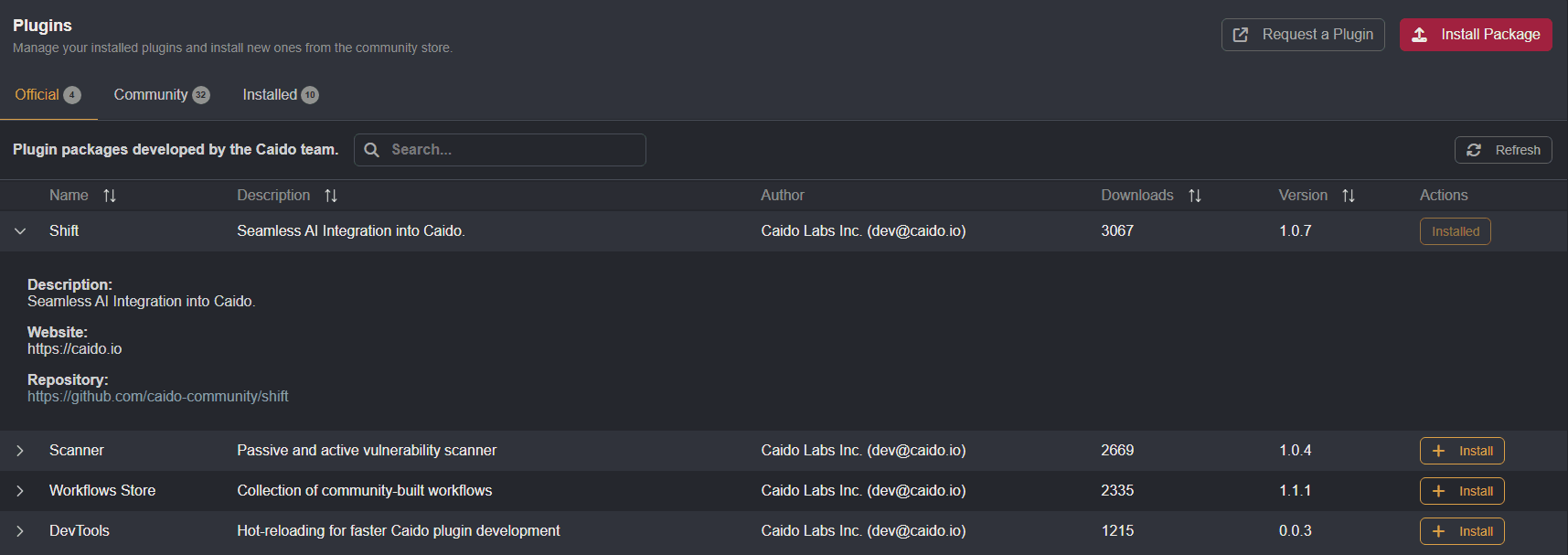
Shift integrates AI/LLM models directly into Caido's user-interface, making the models context-aware. With access to a variety of tools that can carry out actions within Caido, you can submit prompts, written in natural language, to assign tasks to a model of your choosing such as:
Generate a wordlist of common sensitive files that may be publicly exposed.Update this request to reflect this JS:
<response-body-javascript>Create a M&R rule to replace the selected text with: isAdmin=trueFind similar requests to this.TIP
Shift is highly capable and should be able to carry out any task you could do with a well-written prompt.
🧪 CAIDO LABS
Learn how to use this feature in hands-on, simulated training environments: Shift Payload Lab
Configuration
To use Shift, click on the account button in the top-right corner of the Caido user-interface, select Settings, and open the AI tab.
Enter your API key for your provider and click on the Verify button.
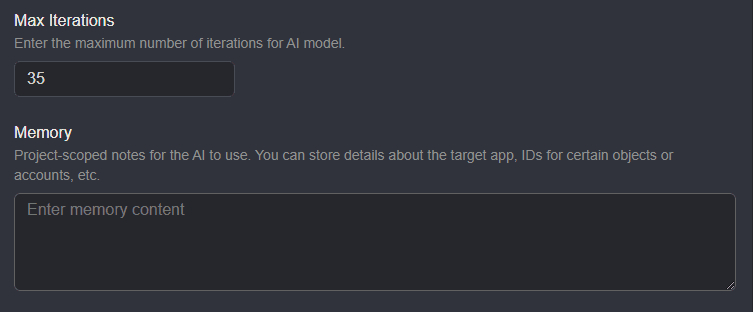
Within the Settings interface of Shift, there are also options to limit the number of API calls a Shift Agent can make and an input field to provide a general system prompt or more contextual information about your target.
Shift Core
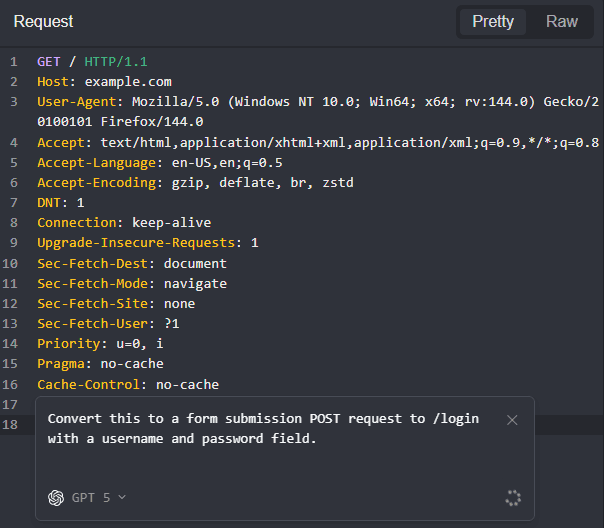
With Shift Core, you can provide direct instructions to the model by using the default keyboard shortcut CTRL + SPACE, typing in a prompt, and pressing ENTER or clicking on the button.
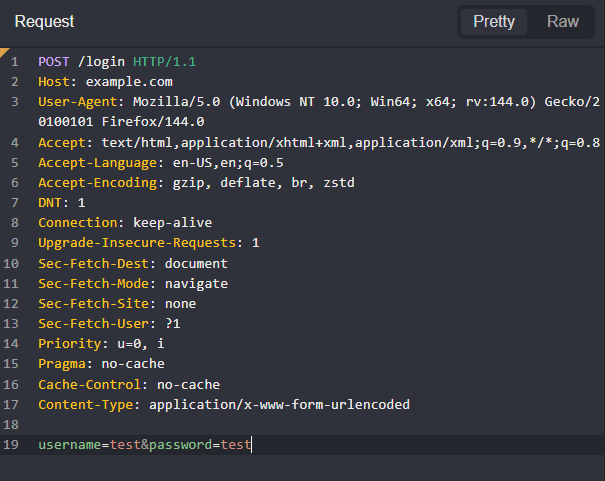
Shift Agents
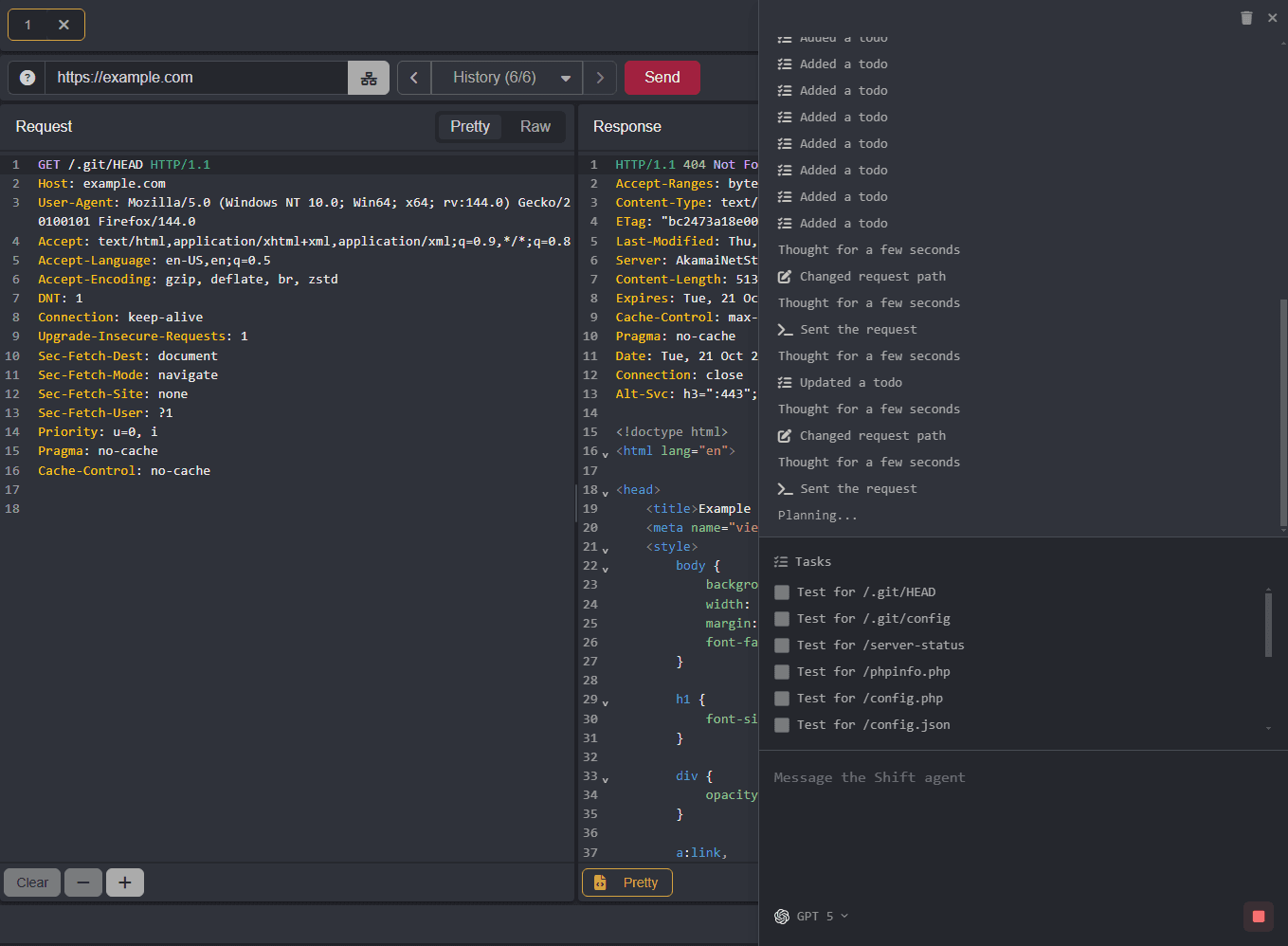
With Shift Agents, you can assign tasks to a model that will be handled autonomously as background processes.
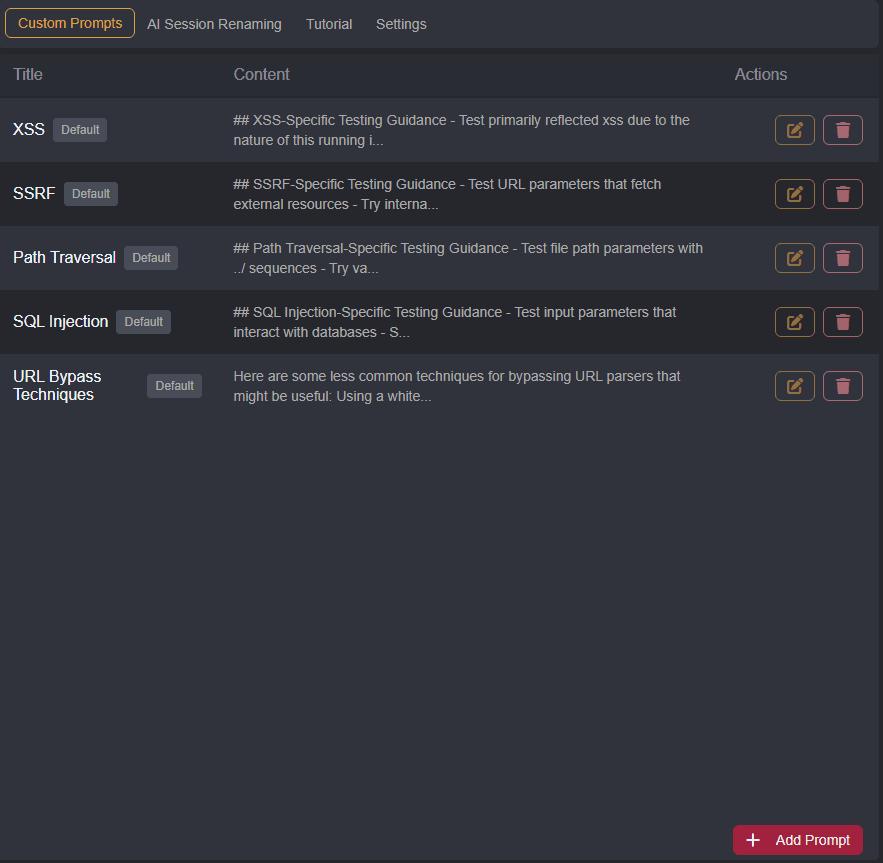
Custom Prompts
For common tasks, you can create and save reusable prompts by clicking on the + Add prompt button within the Custom Prompts tab.
NOTE
When writing custom prompts, provide detailed information and guidelines for the model to follow, such as:
- The root cause of the vulnerability.
- An example of its secure implementation.
- Example payloads or exploitation techniques.
- Examples of commonly vulnerable endpoints or components.
- Indications of successful exploitation.
- Resources to target after successful exploitation.
- Edge cases and similar vulnerabilities.
- Common testing mistakes that may produce false positives.
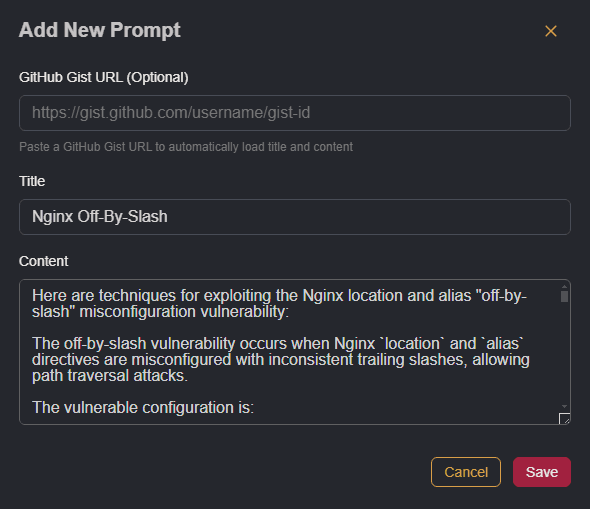
To use a custom prompt, click on the + button within the message input field, select the prompt by name, and reference it in the message.
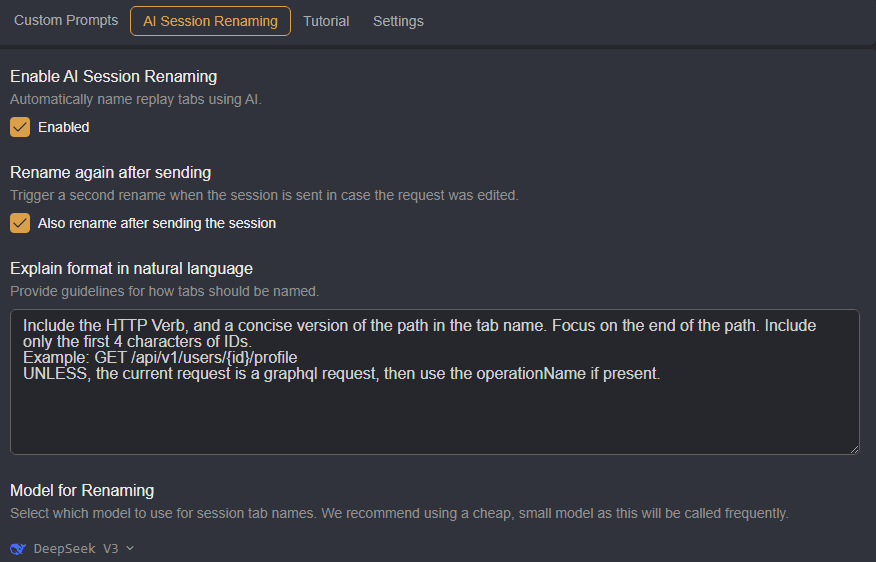
AI Session Renaming
Shift is also able to automatically rename Replay session tabs from their numerical names to descriptive names that identify the purpose of the request. To enable this feature, and configure additional settings, navigate to the AI Session Renaming tab.